Overview
For most enterprises, a breach of their network defenses is a matter of when, not if. Cybersecurity strategies such as anti-virus and perimeter firewalls are prudent and necessary. But no matter the type of attack, all the recently reported breaches have one thing in common: they penetrated the defenses. CISOs, CIOs, Risk Officers, and IT managers want to make their company's information systems resilient so they can continue their critical business processes and protect their precious data—even in the face of a successful attack. They need to be breach-ready.
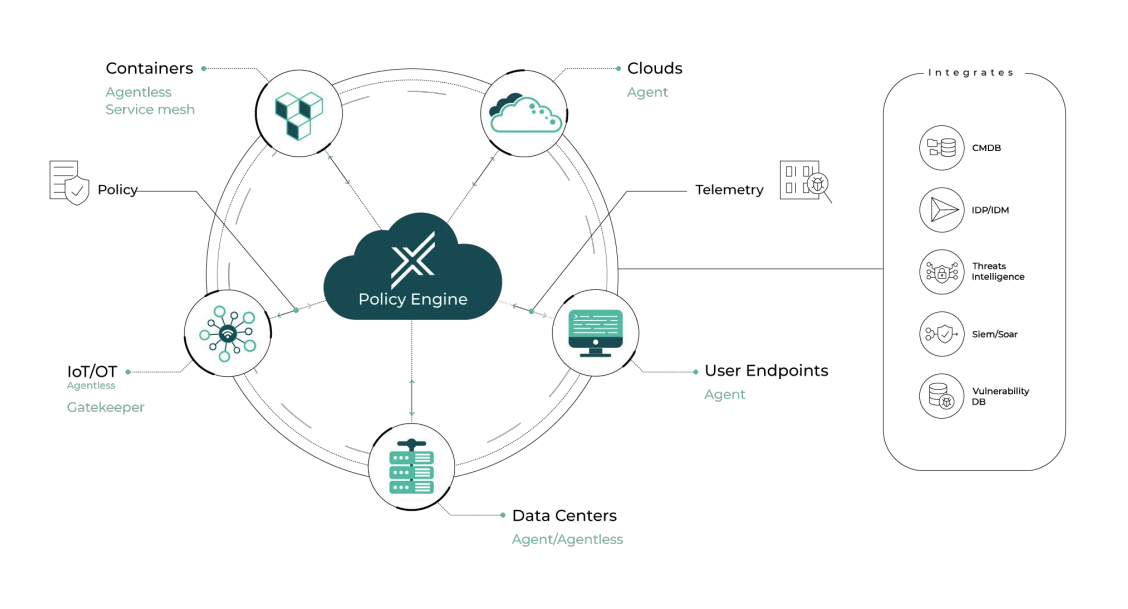
Microsegmentation prevents malware and ransomware from spreading by stopping unauthorized lateral traffic between network resources—preventing catastrophic damage. As a defense-in-depth strategy, it goes beyond perimeter firewalls, VLAN segmentation, and anti-virus solutions by enforcing micro-perimeters around all resources, applications, and endpoints. It's a foundational part of zero-trust security.
With Xshield, you can visualize a map of all your network assets, applications, and their dependencies, and then set up traffic policies to protect them. It lets you manage multiple policy enforcement points, both agent-based and agentless, from one central console, decreasing complexity and saving on training and staffing. Xshield protects all possible points of breach, so there are no soft spots in your proactive cyber defense: data center servers, cloud workloads, Kubernetes containers, user endpoints, OT & IoT devices, and even legacy OS devices.
Get Started
Install Xshield
Learn how to install Xshield using either Docker Compose or on Kubernetes.
Learn more →